Recently I’ve been reading a lot of the Fossil and SQLite code bases. I’ve been very impressed by their cleanliness and the interesting ways in which they break from conventional wisdom in their construction. One thing I stumbled across while perusing a post on the Fossil mailing list was that inetd could be used to create a simple and efficient HTTP server with nothing but some basic C code. My interest was piqued and I began researching inetd on macOS. What I…
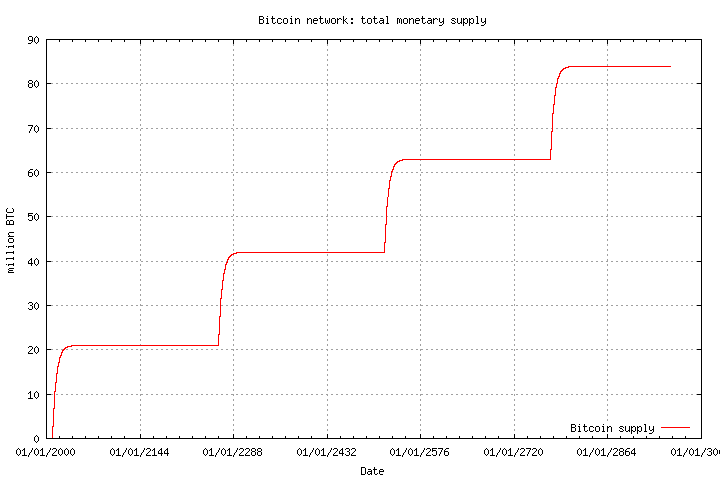
Bitcoin’s fixed monetary supply – 21,000,000 bitcoins – is a fairly well-known fact these days, but there was a time when this wasn’t the case. In fact, until 2014 there was a major bug in Bitcoin that would have caused its supply to inflate forever. If you read the hilarious and short BIP-42 you can get a little bit of insight into what the infinite inflation bug was: As is well known, Satoshi was a master programmer whose knowledge of C++ was…
Sometimes, while working on a project, a simple templating system is necessary either for code or documentation generation. While you can get quite far with sed and awk, their nifty one-liners will eventually become monstrous, especially as your templates get more complex. How do you deal with this growing complexity? For a lot of use-cases the simple m4 macro processor is exactly what you want. This command is probably installed on your machine without you even realizing it. It comes standard…
(Image: Johann Georg Meyer “Das Lesende Mädchen”, 1871) Introduction There is a hidden history to software engineering that some have come to know, but of which most are sadly unaware. Instead, as happens so often in history, a vein of easily graspable but unworkable techniques and ideas has come to dominate the industry. These techniques are bundled with their own superficially plausible justifications and are parroted, easily enough, by amateurs to ensnare other amateurs. And so, we have a generation of…
(Image Wikipedia Commons) Recently I’ve been having a lot of fun following along with Casey Muratori’s Handmade Hero project. As far as I know this is the first time a seasoned game industry vet like Casey has graciously decided to share the step-by-step creation of a professional-quality game. Amazingly, he’s also been including videos detailing every line of code and every major architectural decision. However, following along with the code examples can be tough if you’re not on a Windows…
Recently I’ve been working on a game engine in C++. I’ve always wanted to participate in a Ludum Dare compo, and this work is in preparation for the December 1st compo. A big piece of the design of my engine is using Lua for scripting and providing novel Lua objects from C++ for this purpose. Yesterday I was attempting to embed provide a C++ object to Lua scripts. This object’s lifetime and ownership were managed using a reference counted shared_ptr,…
“New software processes do not just emerge out of thin air; they evolve in response to a palpable need” Software Architecture In Practice, Third Edition 1. Preliminary Throat Clearing Is there something wrong with the way we think about software process? Traditional software processes are often couched in dichotomies: heavy vs agile, bureaucratic vs lightweight, corporate-y vs start-up-y, oppressive vs liberating. Yet dichotomies have and always will obscure gradations of difference and damage our ability for nuanced thinking. Because there…
(Image by Macoto Murayama) NOTE: This post is not necessarily advocating for this approach. I think it’s an interesting idea so I’m putting it out there. This approach, as is, does not account for subjective biases, but it could provide the data to measure and compensate for them. One of the problems I’ve observed with interviews candidates across several companies is their informality. It often feels more like reading tea leaves than finding the best person. While many companies attempt to make this more rigorous, they…
Skepticism emerges as a reaction wherever a certain, commonly held notion of truth begins to unravel. Operating with this notion of truth, we can try to slip out of the grasp of skepticism, but inevitably we trace the same maddening circle right back into its clutches. Can we model this worldview as a machine? Factual Discourse Machines The Classical Factual Discourse Machine We take as our starting point the most naive view of factual discourse possible. All factual discourse involves acts of demonstration. I present…
In this article we’ll discuss writing a disassembler for the Ethereum Virtual Machine (EVM). While writing disassemblers doesn’t necessarily require much knowledge of the machine the instructions are for, it’s actually quite a fun way to get your feet wet. During this tutorial we’ll be using the D programming language. Why D? Honestly there’s no great reason. It’s mostly because I think it’s clearer and simpler than the alternatives for this kind of low-level code. Let’s get started. Introduction When writing…